When you hear about compliance, two acronyms always pop up: AML and KYC. They might seem interchangeable, but they play distinct, complementary roles in protecting your business from financial crime.
Think of it this way: AML (Anti-Money Laundering) is your company's entire strategy for fighting financial crime. It's the big picture—the comprehensive set of rules, monitoring systems, and reporting protocols you put in place. KYC (Know Your Customer) is a critical piece of that strategy. It’s the very first step: verifying who your customers actually are.
Unpacking AML and KYC Compliance

At its heart, Anti-Money Laundering (AML) is the complete playbook your business uses to prevent criminals from cleaning their dirty money through your services. This involves everything from tracking transactions for red flags to filing official reports when something seems off.
Know Your Customer (KYC), on the other hand, is much more specific. It's the hands-on process of identifying and verifying a client’s identity when they sign up and checking in on that information over time. If AML is the war on financial crime, KYC is your frontline intelligence gathering.
How AML and KYC Work Together
You simply can't have a solid AML program without a strong KYC process. It’s impossible. How can you spot suspicious activity if you don't know who your customers are in the first place?
KYC gives you that essential baseline. By confirming a customer's identity, you can build a risk profile and get a feel for what their normal financial behavior should look like. This makes it much easier to spot when a transaction doesn't add up. It’s all about stopping bad actors at the door before they can even get in.
Key Takeaway: KYC is the proactive, upfront work of identifying your customers. AML is the ongoing system of monitoring and reporting that uses the information you gathered during KYC.
To make the distinction crystal clear, here’s a quick breakdown of their core differences.
AML vs KYC Key Differences
This table offers a quick summary highlighting the primary distinctions between AML and KYC.
| Aspect | KYC (Know Your Customer) | AML (Anti-Money Laundering) |
|---|---|---|
| Scope | A specific component focused on customer identity and risk. | A broad framework covering all measures against financial crime. |
| Timing | Primarily at the start of a business relationship (onboarding). | Ongoing throughout the entire customer lifecycle. |
| Main Goal | To verify a customer's identity and assess their risk profile. | To detect and report suspicious financial activity. |
| Core Activities | Collecting ID documents, checking addresses, screening lists. | Transaction monitoring, risk management, filing reports. |
In short, KYC provides the "who," which is the foundation for AML's mission to uncover the "what, when, and how" of potential financial crime.
Why This Matters for Your Business
Ignoring these rules isn't an option. The penalties are steep—we're talking huge fines, legal trouble, and a black eye on your reputation that's hard to recover from. The problem is massive, with the global cost of financial crime estimated to be as high as $2 trillion every year.
That staggering number is why regulators are so tough on compliance. If you want to see the full picture, you can explore more statistics on global financial crime.
Ultimately, getting AML and KYC compliance right isn't just about dodging fines. It's about protecting your business from being used as a pawn in criminal schemes like fraud, corruption, or even terrorism financing. When you see it that way, compliance stops being a chore and becomes a powerful way to build a safer, more trustworthy business.
Building a Risk-Based Compliance Approach
When it comes to AML and KYC compliance, a one-size-fits-all strategy doesn't work. It’s not just inefficient—it’s ineffective. Not every customer carries the same level of risk, and your time and money are best spent focusing on where the real dangers lie. This is the heart of a risk-based approach.
Think of it like airport security. Most travelers go through standard screening. A pre-vetted, trusted traveler might get an expedited lane, while someone on a watchlist will get far more attention. Your compliance program should work the same way, matching the level of scrutiny to the risk each customer brings to the table.
This practical method lets you operate more efficiently without cutting corners on security. It keeps your team from getting bogged down with exhaustive checks on low-risk clients, freeing them up to focus on the genuinely complex cases that need a closer look.
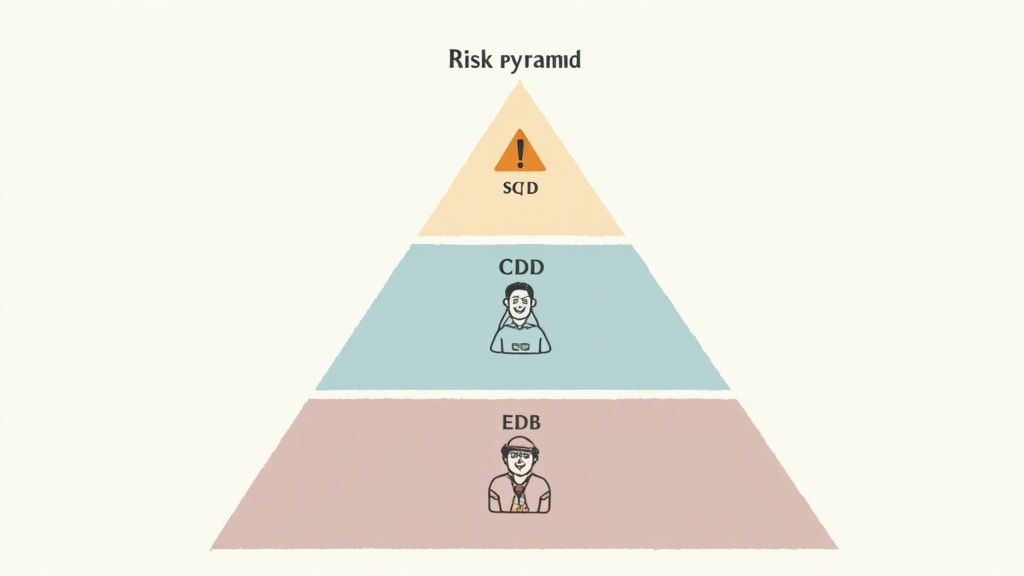
The Three Tiers of Customer Due Diligence
A solid risk-based approach usually breaks down customer checks into three different levels. Each tier comes with its own set of verification steps, designed for the potential risk involved.
-
Simplified Due Diligence (SDD)
This is your baseline check, reserved for clients who pose a very low risk of being involved in money laundering or terrorist financing. Imagine a local charity opening a small bank account or a student applying for a credit card with a tiny limit. The risk is minimal, so the verification process is quick and simple. -
Customer Due Diligence (CDD)
This is the standard level of scrutiny that applies to most of your customers. CDD is your everyday KYC process. It involves collecting and verifying core identity information, getting a handle on why they're doing business with you, and assessing their general risk profile. It’s the standard security check pretty much everyone goes through. -
Enhanced Due Diligence (EDD)
Reserved for high-risk customers, EDD is a much deeper dive. This level of investigation is triggered by specific red flags, like dealing with a Politically Exposed Person (PEP), working with clients from high-risk countries, or onboarding a business with a confusing and opaque ownership structure. EDD means gathering more detailed information on their source of funds and wealth and keeping a much closer eye on their transactions over time.
Creating Customer Risk Profiles
So, how do you decide which tier to use? It all starts with building a customer risk profile. This isn't a one-and-done assessment; it's a dynamic profile you build based on a few key factors.
- Geographic Risk: Where is the customer based? Some countries are known to have weaker AML controls, which automatically raises the risk level.
- Customer Type: Are you dealing with an individual or a complex corporation with a web of offshore accounts? The corporation is inherently riskier.
- Industry Risk: Does the customer work in a cash-heavy business like a casino? Or an industry known for corruption?
- Behavioral Patterns: Do their transactions make sense for their stated line of business? Or are you seeing strange, large, or frequent transfers that just feel off?
By looking at these elements together, you can assign a risk score—low, medium, or high—which tells you exactly which level of due diligence to apply. As you build out this approach, it’s also crucial to implement effective strategies to eliminate data breach risks in BFSI to safeguard all the sensitive data you're collecting.
A strong risk-based approach does more than just tick a regulatory box. It turns your compliance program from a reactive chore into a smart, proactive defense against financial crime. It’s about working smarter, not harder.
This tailored approach is the bedrock of modern AML and KYC compliance. It secures your business without creating pointless roadblocks for your legitimate, low-risk customers.
Getting Customer Verification and Documentation Right

Once you've figured out a customer's risk level, it's time to roll up your sleeves and get to the verification stage. This is where the theory ends and the practical work begins—gathering and confirming the documents that prove your customers are exactly who they claim to be.
Think of it as moving from a calculated risk score to having solid, documented proof in your hands. This isn't just about ticking boxes. It's the bedrock of your entire AML and KYC compliance strategy. Without that solid documentation, you have no real baseline to spot suspicious activity, and that leaves your business exposed to financial crime and steep regulatory fines.
The aim here is to create a crystal-clear, auditable paper trail showing you’ve done your homework. Each document you collect is another brick in the foundation of a trustworthy customer relationship—one that protects your business and the integrity of the financial system.
Core Documents for Individual Customers
When dealing with individual clients, the verification process is usually pretty direct. You have two main goals: confirm their identity and their physical address. This means you'll need to collect a couple of key documents.
-
Proof of Identity: This has to be a government-issued photo ID. We're talking about a passport, a driver's license, or a national identity card. The most important thing is to make sure it's valid and hasn't expired.
-
Proof of Address: This document proves where the customer actually lives. Standard options include utility bills (like gas or electric), bank statements, or official letters from the government. The rule of thumb is that the document must be recent, typically issued within the last three to six months.
These days, just glancing at a document isn't enough. Many businesses are using digital ID scanning to spot fakes and biometric checks to match a live photo to the ID, adding a much-needed layer of security to the whole process.
Verifying Business Entities and Their Owners
Verifying a business is a whole different ball game. It’s more complex because you need to understand its corporate structure and, crucially, find the real people pulling the strings behind the scenes. It's like peeling back the layers of an onion.
A massive part of this is identifying the Ultimate Beneficial Owners (UBOs). A UBO is the actual person who owns or controls a company, even if they aren't listed on the official paperwork. Regulators generally define a UBO as anyone who owns 25% or more of the company or has significant control over its operations.
Uncovering the UBO is non-negotiable. Criminals love using shell companies to launder money, and identifying the real people behind a business is one of the best ways to stop them from using your services.
To do this right, you'll need a specific set of corporate documents.
- Articles of Incorporation or a Certificate of Formation to prove the company legally exists.
- Business Licenses or Permits that are relevant to its industry and where it operates.
- A List of Directors and Major Shareholders to help you map out the ownership tree.
- Proof of Identity and Address for every single UBO you identify, following the same rules you'd use for an individual customer.
The increasing complexity of these rules has pushed global compliance costs to over $60 billion a year. That number really shows how much effort it takes to keep up with what regulators demand.
Managing all this sensitive information requires a secure, well-organized system. Handling these documents efficiently is vital, which is why so many businesses now use specialized software. You can learn more about how a KYC document collection software can automate and secure this entire workflow. It’s an approach that not only keeps you compliant but also creates a much better experience for your customers, turning a potential headache into a smooth, professional process.
How to Build Your AML and KYC Program
Going from understanding the concepts to actually building a program can feel like a massive leap. But the truth is, creating a solid AML and KYC compliance framework is a step-by-step process any business can master. It's all about drawing a clear map with defined roles, rules, and procedures to shield your company from financial crime.
Think of it like setting up a security system for your business. You wouldn't just stick a single camera on the wall and call it a day. You'd name a head of security, scout out vulnerable spots, set access rules, and train everyone on what to do when an alarm goes off. Your compliance program needs that same deliberate, thoughtful approach.
Appoint a Dedicated Compliance Officer
Your very first move is to name a Compliance Officer. This is your go-to person for everything AML and KYC. They'll own the program’s development, rollout, and daily management.
For smaller businesses, this doesn't mean you have to hire someone new. An existing leader, like a CFO or COO, can often wear this hat. The only non-negotiable is that they must have the authority and resources to see the compliance policy through. Clear ownership is key.
Conduct a Thorough Risk Assessment
Before you can write the rulebook, you have to know where your weaknesses are. A business-wide risk assessment is essentially a deep-dive into your operations to pinpoint where you're most exposed to money laundering or terrorist financing.
This review needs to look at a few critical factors:
- Customer Base: Who do you typically work with? Are you dealing with high-risk individuals or serving clients in high-risk industries?
- Geographic Locations: Where are you and your customers based? Certain countries and regions automatically come with higher compliance risks.
- Products and Services: Could any of your offerings, like anonymous payment methods, be particularly appealing to criminals?
- Transaction Methods: How do you handle payments? Businesses that deal with a lot of cash or handle complex international transfers need to be extra vigilant.
The whole point is to build a detailed risk profile for your business. This profile will guide every single decision you make for your compliance program.
Draft and Implement a Formal AML Policy
With your risk assessment in hand, you’re ready to draft your official AML policy. This written document becomes your company's single source of truth for all things compliance. It needs to be clear, thorough, and specifically designed to address the risks you just identified.
Your AML policy isn’t just a stuffy document for regulators—it’s a practical handbook for your team. It turns complex legal jargon into simple, everyday procedures that everyone can follow.
At a bare minimum, your policy has to cover a few core areas:
- A strong Customer Identification Program (CIP) that spells out exactly how you verify who your customers are.
- Procedures for ongoing transaction monitoring to catch and flag anything that looks unusual or suspicious.
- A clear process for reporting suspicious activity to the right authorities, like filing a Suspicious Activity Report (SAR).
- A commitment to regular, independent audits to test whether your program is actually working.
- A plan for ongoing employee training to keep your team sharp on the latest rules and threats.
As you build out these internal systems, don't forget that technology is your best friend. When putting your AML and KYC program together, look into comprehensive compliance solutions that weave in strong cybersecurity measures from the start.
Similarly, the document collection part of your program is absolutely vital and can turn into a huge administrative headache if you do it all by hand. An AML document request tool can automate this entire process, making sure you collect the right information securely and efficiently right from the get-go. This structured approach helps turn a daunting job into a manageable and effective line of defense.
Common Compliance Mistakes and How to Avoid Them
Getting AML and KYC compliance right is a constant challenge. Even with the best intentions, it's easy to make mistakes that can put your business at risk. Honestly, one of the best ways to bulletproof your own compliance program is to learn from the common slip-ups others have made.
These errors usually aren't about cutting corners on purpose. They often come from simple oversights, relying on old ways of doing things, or just not keeping up with a client's changing circumstances. By knowing what these traps look like ahead of time, you can build a much stronger, more resilient defense against financial crime.
Treating Compliance as a One-Time Task
This is probably the most common—and dangerous—mistake I see. A business does a great job with due diligence when a new customer signs up, then they file the paperwork away and never look at it again. That’s a huge miss. Thinking of KYC as a "set it and forget it" task fundamentally misunderstands risk.
A customer's risk profile isn't set in stone. It can, and often does, change. Think about it: a small, local shop you onboarded could get bought out by a multinational firm with a tangled ownership structure, instantly ramping up its risk level. If you're not checking in, you'd never know. You’d be left completely exposed.
The Solution: You need a process for regular KYC reviews. For your high-risk clients, maybe that's a check-in every year. For lower-risk ones, maybe it's every two or three years. The goal is to treat due diligence as a living, breathing process, not a task you cross off a list once.
Neglecting Ongoing Transaction Monitoring
Just as bad is failing to watch what customers do after you’ve onboarded them. A squeaky-clean KYC check doesn't mean much if you ignore their actual transactions. Criminals are patient; they'll often build a history of perfectly normal activity before they try to move dirty money through your system.
Without consistent monitoring, your business is effectively flying blind. You have no way of knowing if a customer’s activity actually matches what they told you, or if it suddenly veers into suspicious territory.
Picture this: a client who usually makes small, predictable deposits suddenly gets a massive wire transfer from a high-risk jurisdiction for no apparent reason. That's a textbook red flag, but you'll only catch it if you have a solid transaction monitoring system in place.
Maintaining Poor or Incomplete Records
Nothing gives a compliance officer a bigger headache—or a regulator a bigger reason to fine you—than messy record-keeping. When an auditor asks for proof of your due diligence, and you can't find it, it's the same as if you never did it at all. Scrambled records make it impossible to prove you did your job and can result in some hefty penalties.
Here's what this often looks like in practice:
- Missing Documents: Not getting a copy of a business license or a key piece of identification.
- Inaccessible Data: Storing customer info in a messy mix of spreadsheets, old email chains, and dusty filing cabinets. You can never see the full picture.
- Outdated Information: Having an expired driver's license or an old address on file because there’s no process to ask for updated documents.
The Solution: A centralized digital system is your best friend here. It keeps all customer verification documents, notes, and communications in one place, creating a clean, organized trail for audits. Simple tools can even send out automated reminders when documents are about to expire, helping you keep everything current.
Providing Inadequate Staff Training
At the end of the day, your compliance program is only as good as the people running it. If your team isn't trained well or often enough, they won't know how to spot red flags or what the correct procedures are. This is the human side of AML and KYC compliance, and you can't afford to ignore it.
An employee who doesn’t grasp why identifying a Politically Exposed Person (PEP) is so important, or who isn’t sure how to report a suspicious transaction, can put the entire company in jeopardy. Regular, practical training turns your team into your most valuable line of defense.
Using Technology to Automate Compliance

Trying to manage AML and KYC compliance by hand is like trying to count every grain of sand on a beach. It’s not just slow and tedious—it’s a recipe for mistakes. This is where technology steps in, turning a mountain of manual work into a manageable, automated process.
Automation doesn't mean replacing your people; it's about making them more effective. When software handles the repetitive, data-intensive tasks, your compliance experts can stop chasing paperwork and start focusing on what truly matters: high-level risk analysis and nuanced decision-making. The right tools do the grunt work so your team can make smarter calls.
Streamlining Key Compliance Functions
Technology can immediately boost the speed and accuracy of your core compliance activities. Manual checks are always vulnerable to human error, but automated systems can execute complex verifications in seconds, giving you consistent and reliable results every single time.
Here are a few key areas where automation really shines:
- Instant Identity Verification: Software can scan and validate official IDs in a flash, checking them against various databases to confirm they’re legitimate. This cuts down onboarding time and dramatically reduces your fraud risk.
- Real-Time Watchlist Screening: Automated tools constantly check customer names against thousands of global sanctions lists, PEP databases, and negative news sources. If a match pops up, you get an alert right away.
- Suspicious Activity Monitoring: Smart algorithms can analyze countless transactions at once, flagging unusual patterns a person might easily overlook. This shifts your approach from reactive problem-solving to proactive risk management.
By automating these core functions, you build a compliance program that is not only more effective but also scalable. As your business grows, your technology can easily handle the increased workload without a proportional increase in costs or staff.
The Benefits of an Automated Approach
Bringing technology into your AML and KYC compliance workflow offers real-world benefits that extend well beyond just ticking regulatory boxes. It strengthens your entire operational foundation.
The upsides are clear: it cuts down on expensive human errors, slashes the operational costs tied to manual labor, and makes sure your compliance efforts can keep pace with your company's growth. A solid piece of document verification software is a perfect example of this in action, transforming a clunky process into a smooth and secure workflow. This frees up your team to tackle more strategic work, knowing the day-to-day compliance tasks are being handled with precision.
A Few Lingering Questions About AML and KYC
Even after you've got the basics down, some practical questions always seem to pop up when it's time to put AML and KYC compliance into action. Let's tackle some of the most common ones to clear up any confusion.
What Triggers an EDD Check?
Think of Enhanced Due Diligence (EDD) as the extra security screening at the airport. It isn't random; specific red flags pull a customer out of the regular line for a closer look because they represent a higher risk.
So, what are these triggers? Usually, it's one of these things:
- Politically Exposed Persons (PEPs): Anyone in a prominent public position is automatically considered higher risk. It’s not that they are corrupt, but their influence and access make them a bigger target for it.
- High-Risk Jurisdictions: If your customer is from or does business in a country with a reputation for lax AML rules or corruption, you'll need to dig deeper.
- Complex Business Structures: When you can't easily tell who owns a company because of shell corporations or a confusing web of trusts, that's a major red flag. Transparency is key.
- Unusual Transaction Patterns: A customer suddenly making large, frequent, or just plain weird transactions that don't fit their profile will definitely get your attention and trigger an EDD review.
How Long Must We Keep KYC Records?
Keeping good records isn't just a good idea—it's a hard-and-fast rule. Regulators need to be able to look back and see the work you did to vet your customers. If they come knocking, you need a clear, auditable trail.
While the exact timeline can change depending on where you are, the global standard is pretty consistent.
Most regulators, including the big one—the Financial Action Task Force (FATF)—say you need to hang on to all customer ID data and transaction records for at least five years after you've parted ways with the customer. That way, if an investigation pops up years later, the evidence is ready and waiting.
Are AML and KYC Only for Banks?
That’s a myth, and a dangerous one. Banks are certainly on the front lines, but the rules now apply to a much wider playing field. The goal is to protect the entire financial ecosystem from being exploited.
Key Insight: If your business moves or holds money or other assets for customers, criminals see you as a potential tool. Regulators know this, and they've widened the net.
Today, you'll find strict AML and KYC compliance rules in all sorts of industries, including:
- Real estate agencies
- Law firms and accountants
- Jewelers, art dealers, and other high-value goods sellers
- Casinos and money transfer services
- Crypto exchanges and other virtual asset providers
Bottom line: if your business could be used to hide where money came from, you probably have compliance obligations. Always check the specific rules for your industry and location. The scope is much broader than most people think, and ignorance isn't an excuse.
Ready to stop chasing documents and start building a smarter, more efficient compliance workflow? Superdocu provides the tools you need to automate document requests, track expirations, and create a seamless experience for your clients. Discover how Superdocu can transform your compliance process today!
